Framework Engineering - Computer Science
Here is solutions for Framework Engineering - Computer Science.
1. How to implementation ? - Pattern Oriented
- Optimize idea: Brute Force first → Optimize in ideas
- Use patterns for implementation ⇒ You good at idea, but stuck in implementation because you do not remember patterns.
2. Computer Architecture Knowledge
- CPU Cycle
- Mỗi CPU nó ping theo block
Cycle time = 1 / f- 2 GHz CPU → 1 cycle = 0.5 ns
- 4 GHz CPU → 1 cycle = 0.25 ns
- Mỗi CPU nó ping theo block
- Stall/Hazards
- Stall
lw r1, 0(r2) add r3, r1, r4- Cycle 1: lw in EX
- Cycle 2: lw in MEM (data not ready yet)
- Cycle 3: add wants r1 → NOT READY ⇒ Add stall here
- Hazards:
- Hazard causes a stall, but a stall is the result.
- Data hazard:
addneedsr1lwhasn’t finished yet
- Control hazard
if (x > 0) { A(); } - Structural hazard
| Cycle | IF | ID | EX | MEM | WB |
| —– | ——– | — | — | — | — |
| 1 | lw | | | | |
| 2 | add | lw | | | |
| 3 | ❌ stall | add | lw | | |
| 4 | next | ❌ | add | lw | |
| 5 | | | ❌ | add | lw |
- Cycle 3:
- lw needs data memory (MEM)
- add needs instruction memory (IF)
- Cycle 3:
- Data hazard:
- Hazard causes a stall, but a stall is the result.
- Stall
-
Struct Padding and Init by 32-bit (4 bytes), 64-bit (8 bytes) padding
-
Based on architect: 32-bit or 64-bit, so it store the padding of the OS differently ⇒ But need to divide by 4 bytes or 8 bytes like this.
struct Good { int i; // 4 bytes char c; // 1 byte char d; // 1 byte }; i -> 4 bytes c -> 1 byte d -> 1 byte pad -> 2 bytes Total: 8 bytes -
The compier maybe re-order the struct for better init padding, or aware about the memory address.
-
-
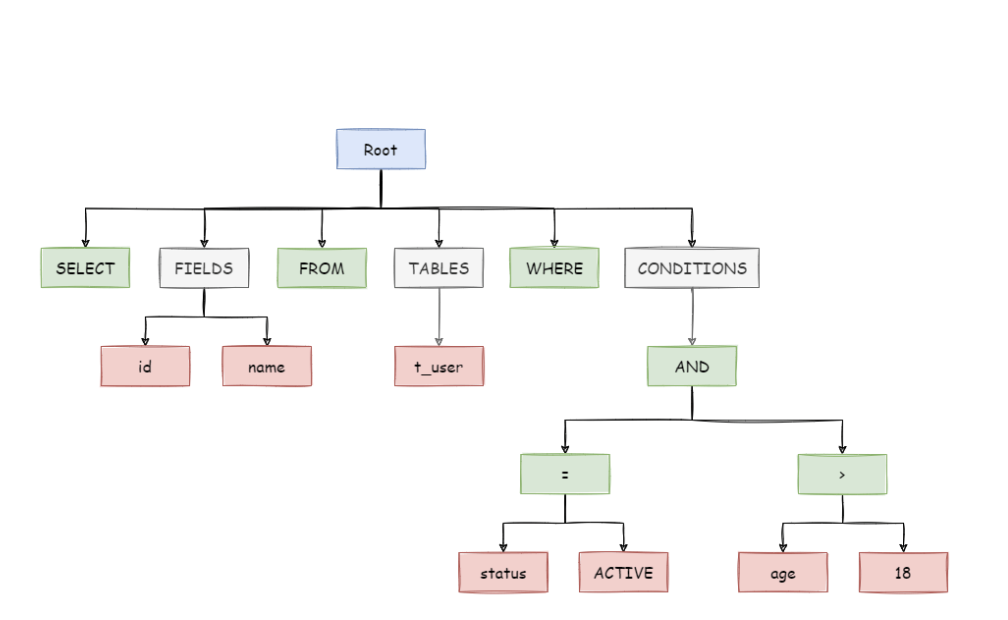
SQL Parser
5. Network
1. TCP 3-way handshaking ?
- Client sent SYN packet to the server with sequence num A
- Server sends SYN-ACK packet to the client with rand sequence num B and ack num A' = A+1
- Client sends ACK packet to the server, with ack num B' = B+1 and the sequence number is A' ( the ack num it received in step 2)
2. Why 3-way handshaking but not 2-way handshaking ?
- 2-way will establish a half-duplex connection: client → server.
- 3 way is full-duplex transaction: server → client.
3. What is syn, ack mean?
- Syn means synchronizaton: SYN packet is sent when the sender tries to connect to the receiver.
- Ack means acknowledgment: ACK packet is sent by the receiver to the sender to help the sender know that the SYN packet that it sent before reached the destination successfully.
4. Sequence numbers: 32 bit, value 2^32 - 1
- So if the amount of data is greater than 4GB, at least one sequence number value will be reused.
5. What if the 3rd handshake fail? How the server can detect it and what does it do in this case?
- Based on ack number ⇒ Know what message in range [1000, 30000] is missing.
- Retry and back propagation ⇒ Dynamic retry based on **Round-Trip Time (RTT)**
6. **Checksum:** Check source IP, destination IP, payload
7. Sequence and byte-range: know the missing packet.
8. **How TCP close the connection?**
- 4-way handshaking
- Step 1: Client send FIN
- Step 2: Server accept
- Step 3: Server send FIN
- Step 4: Client accept.
9. How Ping command works?
- Calculate RTT based on when ping and receive message.
10. What is TTL? How does TTL will be changed?
- To make sure the packet do not stuck forever in the Internet.
- Default TTL = 64, after reach the router TTL minus 1 ⇒ If it is 0, it is discard, send ICMP to the sender.
11. HTTP Protocol
- Add some header fields: Method, POST, PUT, GET.
- Add cookie to the cookie.
- Session is generated in layer 6 with session ID, end when you kill the tab. **AJAX technique?**
12. AJAX technique?
- A for asynchronous.
- Make API call without reload the page.
13. OSI Model
- L7: Browser creates HTTP request - Application layer
- L6: Data is encrypted using TLS, encode JSON, UTF-8
- L5: Session is established - Server know which client is - Keeps the connection alive. Use session_id to stateful in browser => auto gen.
- L4: Data is segmented into TCP packets
- L3: IP address is added
- L2: MAC address is added, ARP protocol (Address Resolution Protocol) - You only find the MAC address of the next hop (your router).
- L1: Bits are transmitted over the cable
14. DNS lookup (in case you already access google.com before and also in case you do not know the IP of google.com)
- Find in root DNS server ⇒ .com, .net,…
- Find top level domain
- Find authorized server.
15. Maximum port
- Source port: 16 bit.
- Destination port: 16 bit.
- Source IP, Destination IP: 32 bit.
- Total socket connection: 2^16 - 1
```jsx
a . b . c . d
8 bits 8 bits 8 bits 8 bits
=> 28=256⇒0 to 255
```
16. Socket
- When TCP connection is establish.
- It create a socket connect to connect between 2 server.
- Client: random port, Server: port 80
```jsx
Client: 192.168.1.10:53422
Server: 93.184.216.34:80
```
17. Do 2 processes same socket ?
- It’s ok, and this is call multi cast.
18. IP and MAC Address:
- IP: tell who we will send data.
- MAC: how the data transfer through router.
19. What is buffer? why we always need buffer when working with "file"?
- When the process is processed, store this in the buffer of the memory.
6. OS
1. Process and Thread
- Process: independent program loaded to CPU.
- Thread: a single unit execution in the process
2. Context switch in process and thread
- Context switch in process stored in PCB.
- Context switch in thread stored in TCB.
- But context switch in thread required ⇒ Page replacement, or page swap
3. Virtual memory
- When a program load to memory ⇒ load to virtual memory
- Virtual memory = 8GB RAM + 16 GB Disk.
4. Two process can access through the same physical address ?
- Yes, if virtual memory point to the same physical address.
5. Process has how many states? How does it change between each state?
- Process have 5 states: new, ready, running, wait, and terminate
- PCB contains something: variable, memory, next command to process.
6. Can two processes communicate with each other ?
- Shared memory or message passing
7. What is child-process? How to create a child-process?
- Child process is copy-on-write from parent.
- But it is independent process, only communicate with parent through shared memory and message passing.
8. Deadlock
- Mutual exclusion: access same resource.
- Hold and wait: each process hold, other need to wait.
- No preemption: wait too long to execute.
- Circular wait
9. CPU Algorithm scheduling
- FCFS, SJF, Round-robin, SRJF, Priority Queue
10. Mutex, Semaphore, Read-write lock
- Mutex: access same resource.
- Semaphore: limit of resource pool.
- Read-write lock:
- Write lock: Only one thread can hold it, when write lock all.
- Read lock: do not lock.
11. What process data contains:
- Text section: code
- Data section: global and static variable.
- Stack section: local variable
- Heap section: dynamic allocation variable or object.
12. File description in Linux
| FD | Meaning |
| --- | ------------------------ |
| `0` | stdin (keyboard) |
| `1` | stdout (terminal output) |
| `2` | stderr (error output) |
13. User mode, kernel mode, system call
- User mode: only access user data, limit some permissions like i/o modify file system.
- Kernel mode: Can do all things.
- System call: change from user mode to kernel mode.
```bash
ls
Multiple syscall: openat() -> getdents64() -> ...
```
14. File system in Linux
- Regular File
- Directory
- Pipe: process intercommunication
- Socket: from host to internet.
- Device Files
15. Garbage collector
- Each language have this
- Idea of Java is: Young Generation, Old Generation, Adult Generation, Permanent Generation
7. Database
- 3 types of normalize data
- Type 1: Each field 1 value.
- Type 2: Split table for PK → A, PK → B,…
- Type 3: Split table B → C, B → D ⇒ Split B → C, B → D, although B is not PK
- Dirty read, Non-repeatable read, Phantom read
- Dirty read: read the value uncommited.
- Non-repeatable read: in the same transaction, have 2 different value when different transaction have committed.
- Phantom read: Same query but query again have value
- 4 isolation level
- Read uncommited
- Read committed: solve dirty read.
- Non-repeatable read: solve repeatable read.
- Serializatable: solve phantom read too.
December 16, 2025
